Telnet over Internet
A couple of days ago Cisco released a Security Advisory . No big deal so far, level was informational so I didn’t read it right away.
Title is impressive:
Cisco Best Practices to Harden Devices Against Cyber Attacks Targeting Network Infrastructure
so i read it during a lunch break just to be aware of the contents.
Management sessions to network devices provide the ability to view and collect information about a device and its operations. If this information is disclosed to a malicious user, the device can become the target of an attack, compromised, and used to perform additional attacks.
Ok, I agree so far.
Because information can be disclosed in an interactive management session, this traffic must be encrypted so that a malicious user cannot gain access to the data that is transmitted. Traffic encryption allows a secure remote access connection to the device. If the traffic for a management session is sent over the network in clear text (for example, using Telnet on TCP port 23 or HTTP on TCP port 80), an attacker can obtain sensitive information about the device and the network.
This doesn’t sound good. The advisory explains why it’s not a good idea to use any clear text management protocol and recommends to use SSHv2 along with other common sense hardening that should be well known to any network engineer.
Why a big vendor like Cisco feels the need to publish that advisory?
The main reason is because there actually is people out there configuring network devices and permitting access via SNMPv1/v2, Telnet and other insecure protocols.
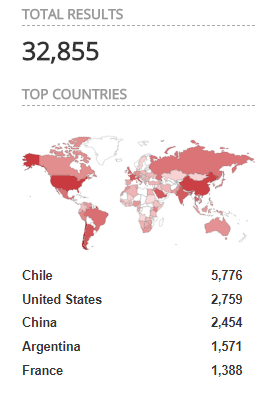
A quick search on Shodan with keywords
port:23 cisco
Gives a huge number of results:
These are all Cisco boxes accessible via Telnet via Internet. Are all these honeypots ?
Basic training
On Cisco’s CCENT/CCNA ICND1 Official Exam Certification Guide , the most basic book for the lower level of certification, on Chapter 8 we can find:
The key difference between Telnet and SSH lies in the fact that all the communications are encrypted and therefore are private and less prone to security risk.
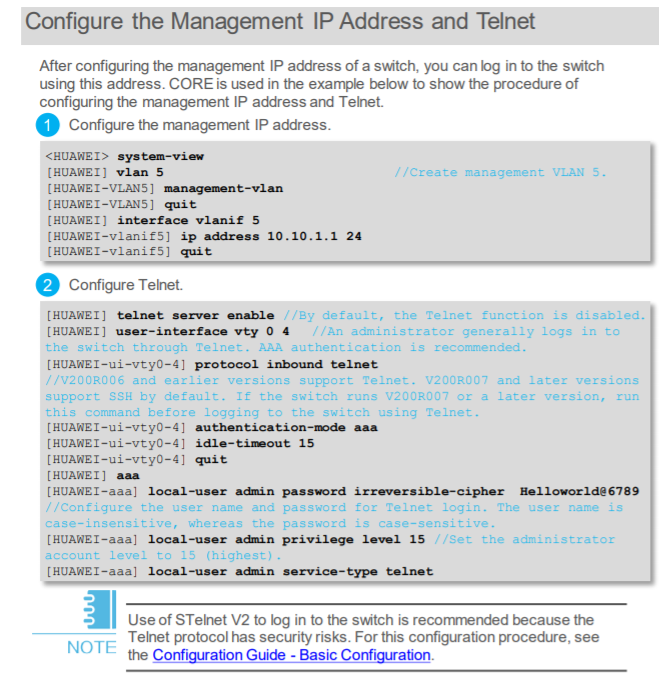
Other vendors, Huawei for example, still put telnet in their documentation but a note recommends to use STelnet v2 a.k.a. SSHv2
Source: S Series Campus Switches Quick Configuration
I do occasionally networking training for customer and colleagues. How to properly access devices for management is a topic being discussed in the first hour.
It’s all about money
I posted on my twitter account :
I think your reading comprehension is spot on. Chicken are coming to roost after years of neglecting the workforce.
— Marko Milivojević (@icemarkom) April 17, 2018
and Marko’s reply completes my reasoning.
Investments in security products today make sense only when including training of all levels of people involved in the technical process.
Any intern or junior network engineer can configure a basic networking device, but lack of the basic training can have a big impact on the network security.
Order of Networkers?
Sometimes I discuss with my colleagues if some kind of professional qualification should be required for people working in IT.
For doctors, journalists and lawyers there are qualification and registers to allow people to do the job. Even the guy who installed my boiler has technical qualifications from the vendor and must issue a certificate of conformity after installation and maintenance. Same process for my house electrical system, hydraulic and so on.
I’m not sure something similar would be possible but maybe the IT industry needs a better criteria than cost to chose professionals.
Ideas?